Tag: privacy

Medjacking is a Real Threat to Health Care Systems
Medjacking, or medical device hijacking, is a new kind of cybersecurity threat to health care systems. Medjacking involves hacking into medical devices using backdoors to access software on the device. Since many of the vulnerable medical devices, such as life-support equipment and diagnostic equipment, use older or standard operating systems, the biggest challenge for a… READ MORE

Cybercrime Now a Bigger Worry Than Physical Crime
Cybercrime and data breaches have been on the rise for many years, and it is not surprising that the threat of cybercrime has become a bigger concern for people than the threat of real, physical criminal acts. A recent report issued by Sophos, Ltd. indicates that people are now more worried about being the victim… READ MORE

Yahoo Data Beach: One Billion Users Exposed
The Yahoo data breach is one of the largest cyber security hacks to happen to date. Yahoo recently announced that it was the victim of a cyber attack in August of 2013, and this revelation could have an impact on Yahoo’s potential sale to Verizon. Yahoo revealed that more than one billion Yahoo user accounts may… READ MORE
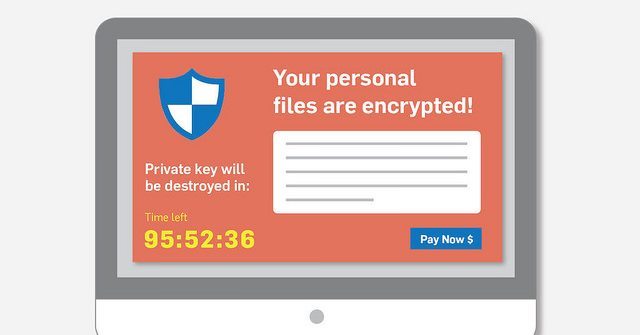
New Ransomware Offers Victims a Hobson’s Choice: Pay Up or Infect Two Colleagues
There is a new ransomware making the rounds that offers victims a Hobson’s choice: Popcorn Time ransomware. This ransomware gives the victim a choice: either pay the ransom amount to gain access to his or her data, or choose to pass the ransomware on to two unsuspecting colleagues. It hardly sounds like a choice, does… READ MORE

Quest Diagnostics Data Breach: Another Healthcare Hack
The Quest Diagnostics data breach is the most recent health care entity to be affected by security hack in 2016. In late November, Quest Diagnostic, a medical laboratory company used by countless health care entities nationwide, announced that it had recently identified itself as a victim of a data breach. According to the company, an unauthorized… READ MORE

Going Phishing: Malware and It’s Role in Data Breaches
Malware is a malicious type of software code that plays a significant role in data security breaches. Malware is typically deployed through a phishing email message scam. This involves an unsuspecting victim receiving an email message from a fraudulent source, a victim clicks on a nefarious link or opens an attachment of the email that contains the… READ MORE

OPM and U.S. Military Data Breaches
In the hacking world, a few of the most favored data breach targets include governmental agencies and militaries. Whether it is the challenge of hacking these presumably highly secure entities, or the thrill and notoriety associated with a successful hack, governments and militaries are constantly subjected to cyber threats. In particular, the United States government… READ MORE

What are Data Breach Notification Laws?
What are data breach notification laws? Many people have heard about, or have themselves been potentially victimized by a data breach. Your credit card information might have been hacked, or your personal identifying information might have been exposed in a data security breach. But many people do not realize that there are legal protections in… READ MORE

Businesses Must Prepare for Data Breaches
Data breaches involving businesses are happening all the time. The best way for a company to deal with a hack is to prepare for data breaches before it happens. It does not matter what size your business is, if hackers can easily access personal information stored in your company’s system, they will find a way. Businesses are… READ MORE

How to Respond to a Breach of Customer Data
How do you respond to a breach of customer data? If you operate an ecommerce store, you need to know. Revision Legal partner John DiGiacomo has published another article on Practical Ecommerce: How to Respond to a Breach of Customer Data. Data breaches seem to be the norm these days, whether they are at Yahoo, Home… READ MORE